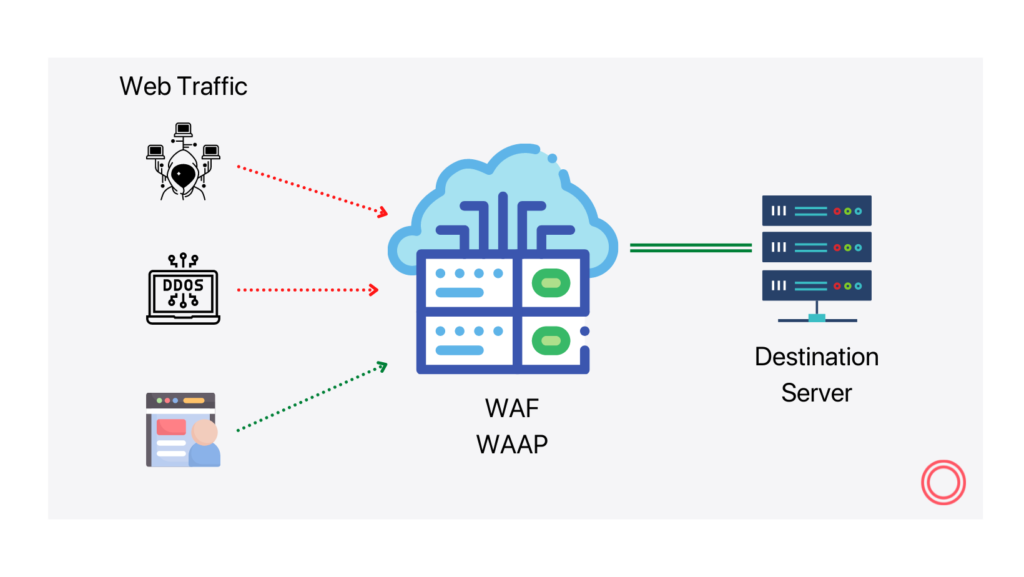
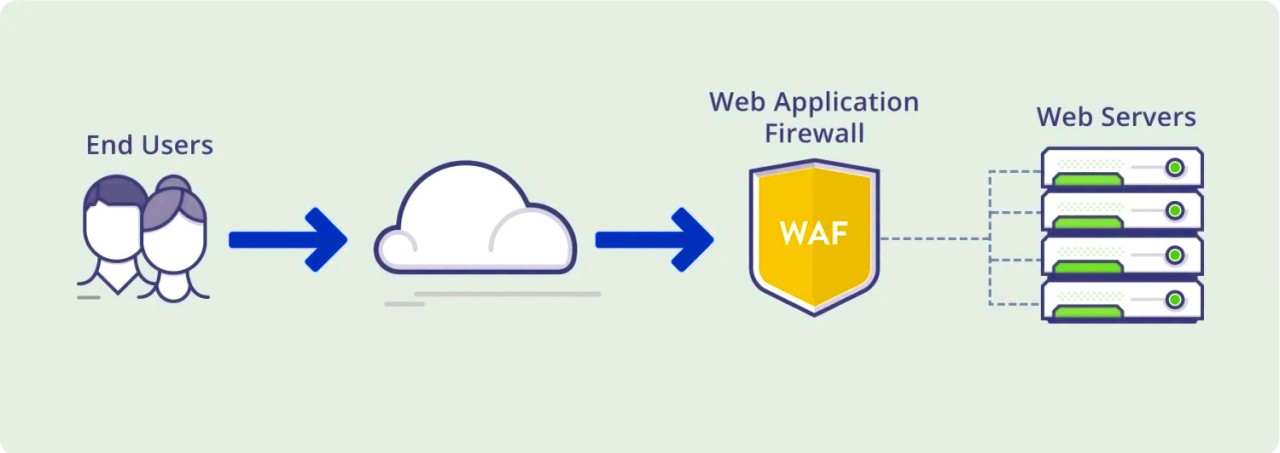
Using Web Application Firewall at container-level for network-based threats
Por um escritor misterioso
Descrição
The microservices architecture provides developers and DevOps engineers significant agility that helps them move at the pace of the business. Breaking monolithic applications into smaller components accelerates development, streamlines scaling, and improves fault isolation. However
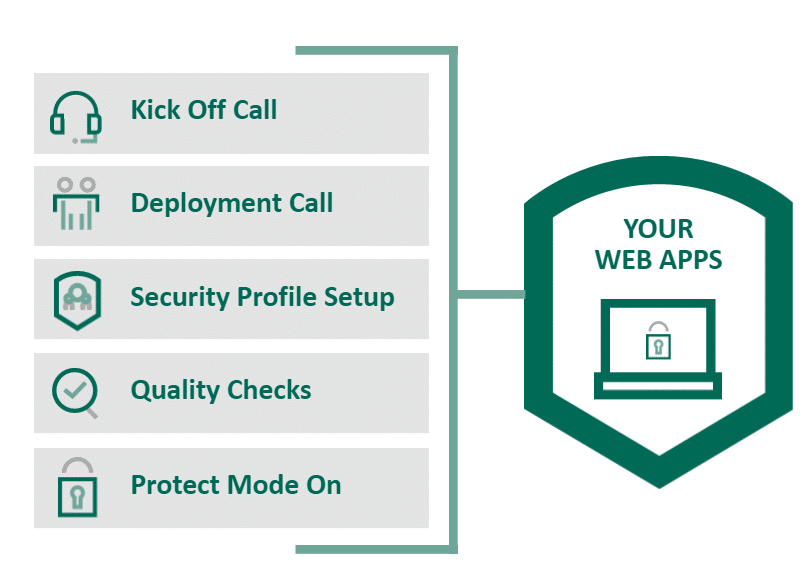
Managed Web Application Firewall (WAF)

Managed Web Application Firewall (WAF)

Qualys TotalCloud™: Cloud-native Security Solution

CYBER SECURITY True Digital Group
What Is Zero Trust Security? How to Implement It & More
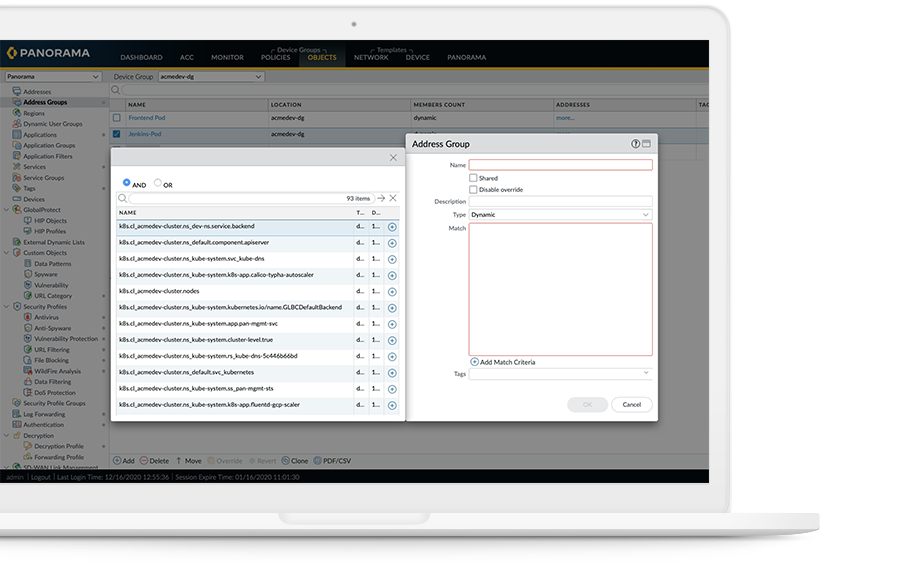
CN-Series Container Firewalls for Kubernetes - Palo Alto Networks
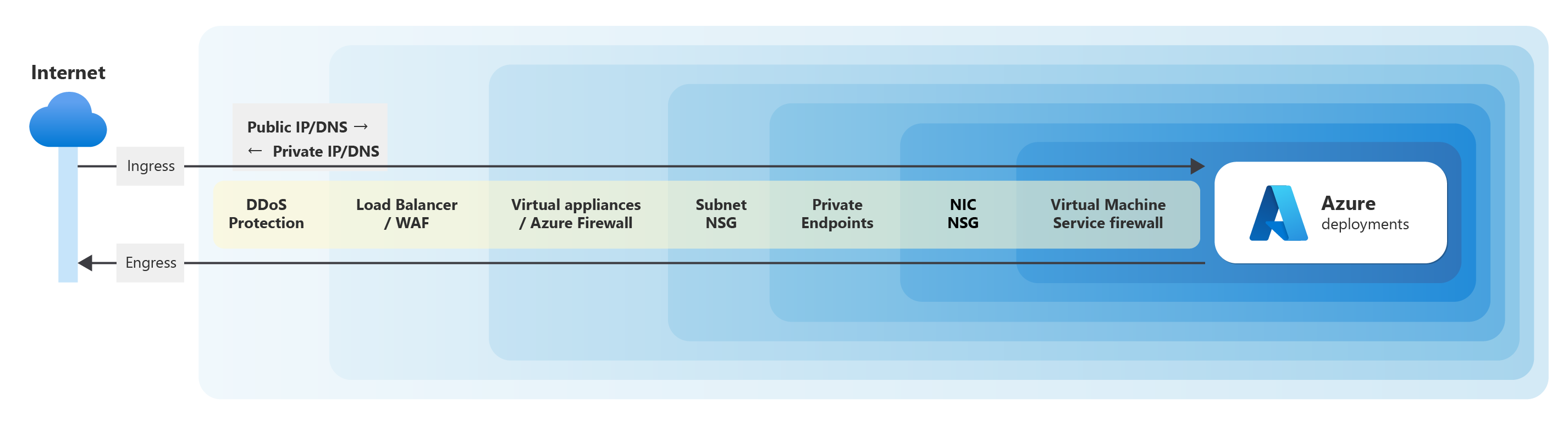
Recommendations for networking and connectivity - Microsoft Azure Well-Architected Framework
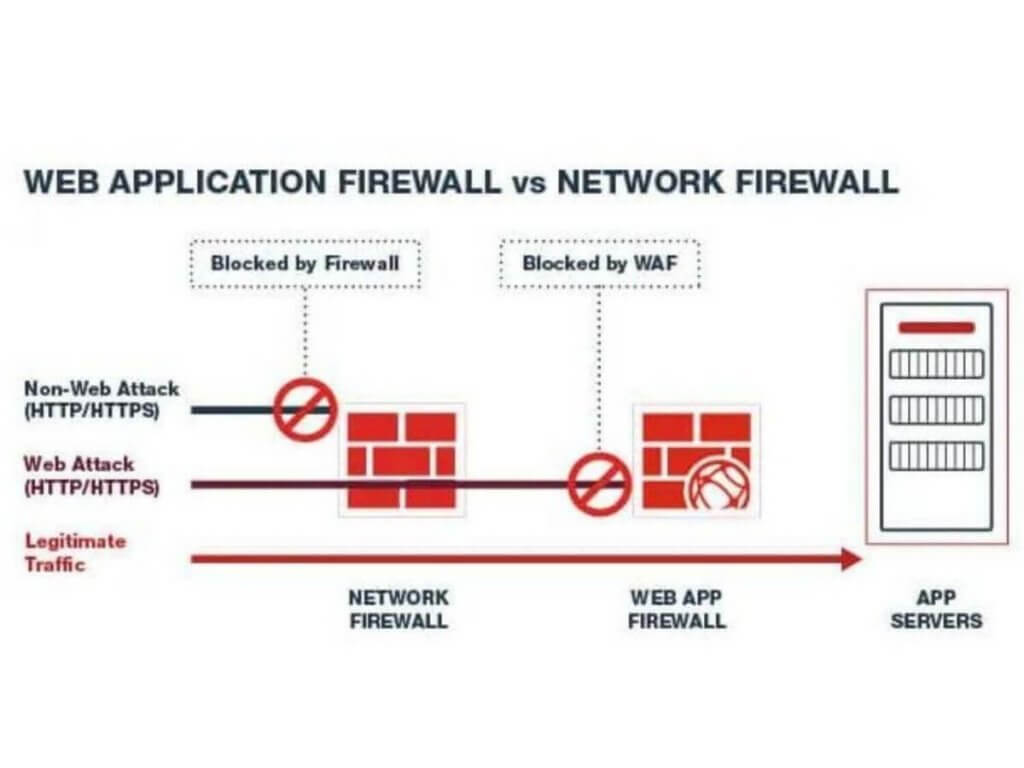
Understand WAF or Web Application Firewall
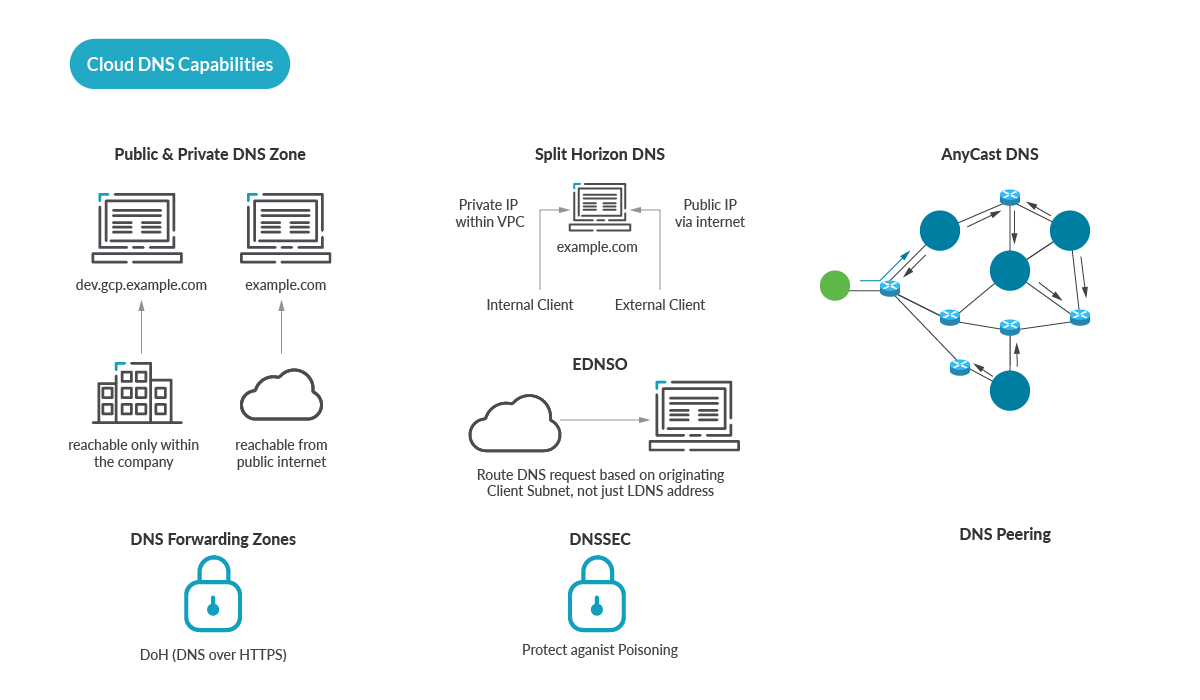
Cloud DNS Security - How to protect DNS in the Cloud – Sysdig
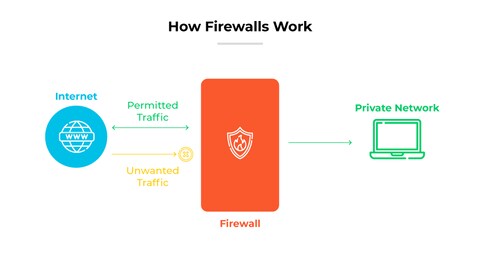
What is a Firewall? Firewall Definition - Palo Alto Networks
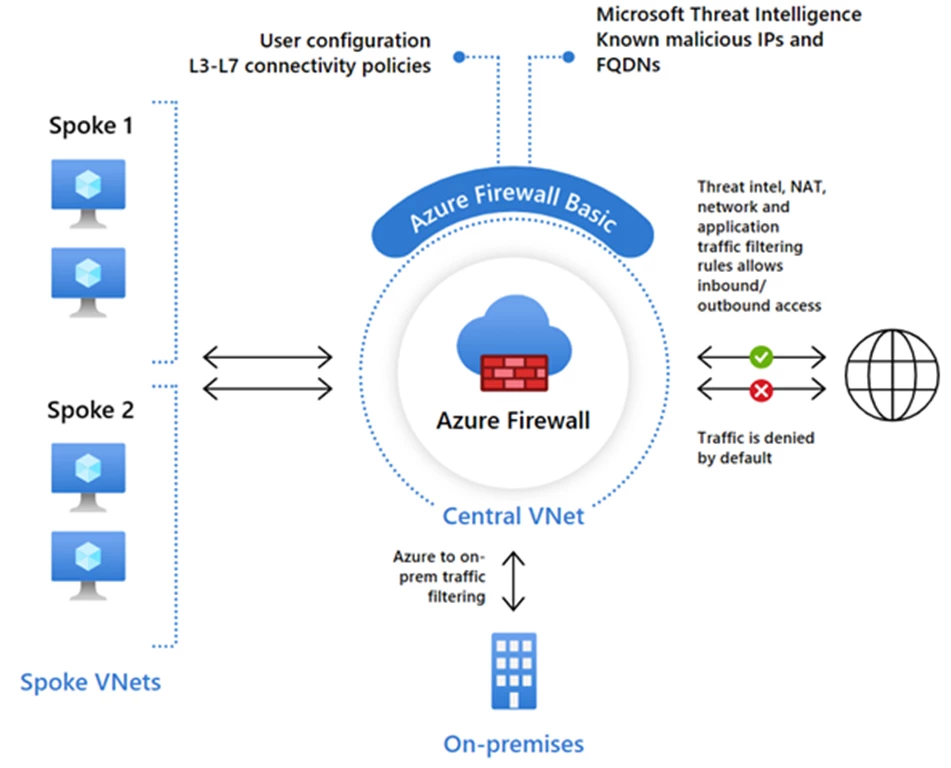
Protect against cyberattacks with the new Azure Firewall Basic
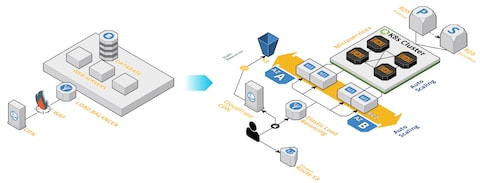
What Is a WAF? Web Application Firewall Explained - Palo Alto Networks
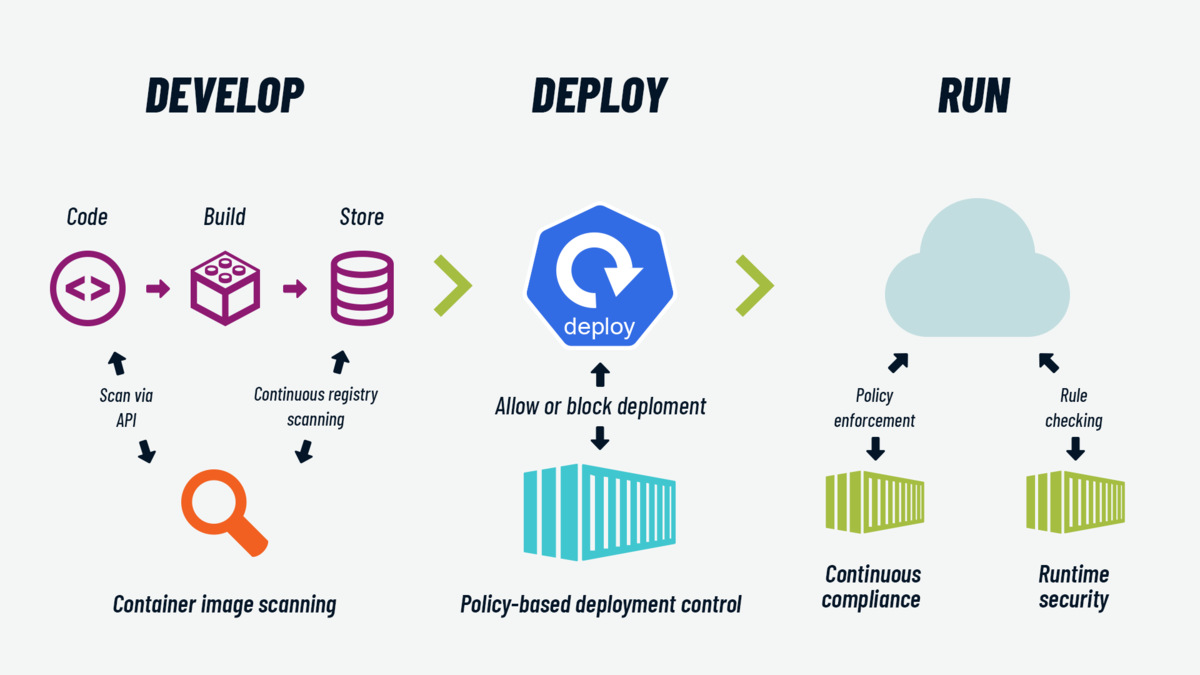
Container Security: what it is and how to implement it
de
por adulto (o preço varia de acordo com o tamanho do grupo)