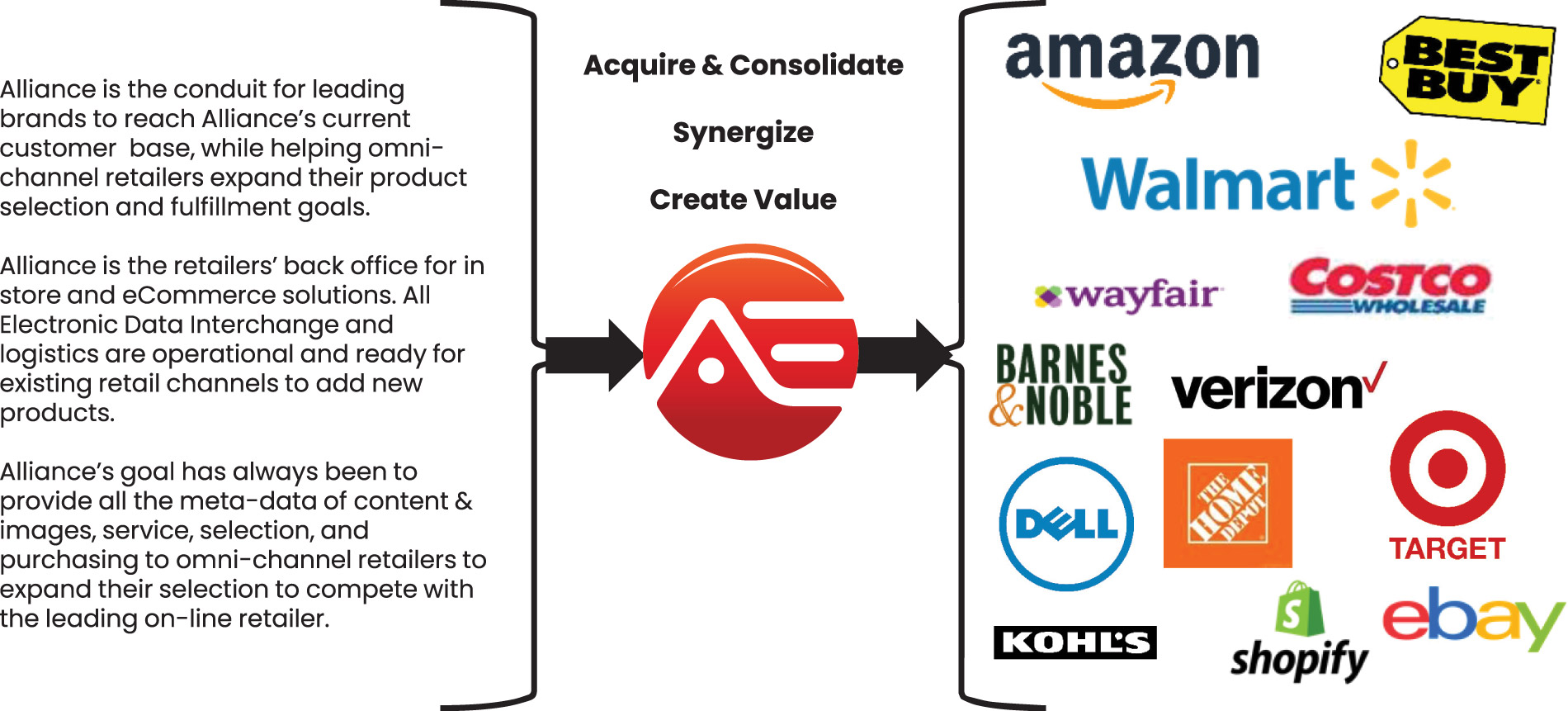
Lone-Actor Terrorism: Policy Paper 2: Attack Methodology and Logistics
Por um escritor misterioso
Descrição

HIGH-RISK SERIES Efforts Made to Achieve Progress Need to Be Maintained and Expanded to Fully Address All Areas

Feature Commentary: Elements of a Pragmatic Strategy to Counter Domestic Political Violence – Combating Terrorism Center at West Point

Reshaping policies for creativity: addressing culture as a global public good

Hackers use a new technique in malspam campaigns to disable Macro security warnings in weaponized docs

PDF) Analysing the Processes of Lone-Actor Terrorism: Research Findings

How Afghanistan's Overthrown Governing Elites Viewed the Violent Extremism Challenge – Combating Terrorism Center at West Point

Lone-Actor Terrorism: Policy Paper 2: Attack Methodology and Logistics

PDF) Lone-Actor Terrorism Policy Paper 2: Attack Methodology and Logistics
tm239600-23_424b4alt - none - 24.7188496s

Personal Characteristics of Lone-Actor Terrorists International Centre for Counter-Terrorism - ICCT

Lone Actor Terrorism: Database International Centre for Counter-Terrorism - ICCT

The Future of European Security: What is Next For NATO - CEPA

The Military, Police, and the Rise of Terrorism in the United States

EvilProxy used in massive cloud account takeover scheme

Oct. 11: IDF widens strikes on Gaza
de
por adulto (o preço varia de acordo com o tamanho do grupo)

/cdn.vox-cdn.com/uploads/chorus_image/image/71836260/1246047198.0.jpg)


