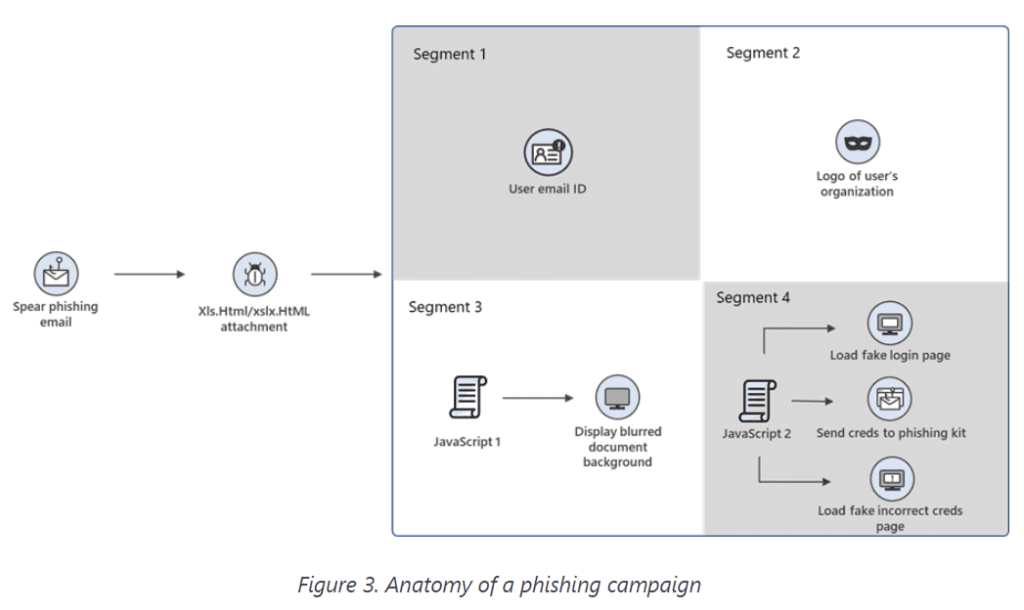
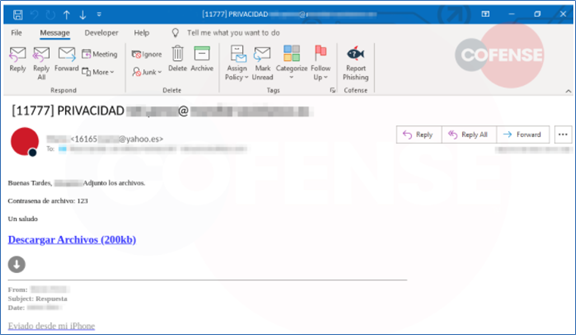
How ransomware attackers evade your organization's security
Por um escritor misterioso
Descrição
How ransomware operators avoid your security solutions and what you can do to protect your network against post-compromise ransomware attacks.

Anatomy of the Kaseya Ransomware Attack and How to Avoid the Headlines - Coretelligent

9 Best Practices to Avoid Ransomware Infection

How to Detect and Prevent Ransomware Attacks?

The realities of ransomware: The evasion arms race – Sophos News
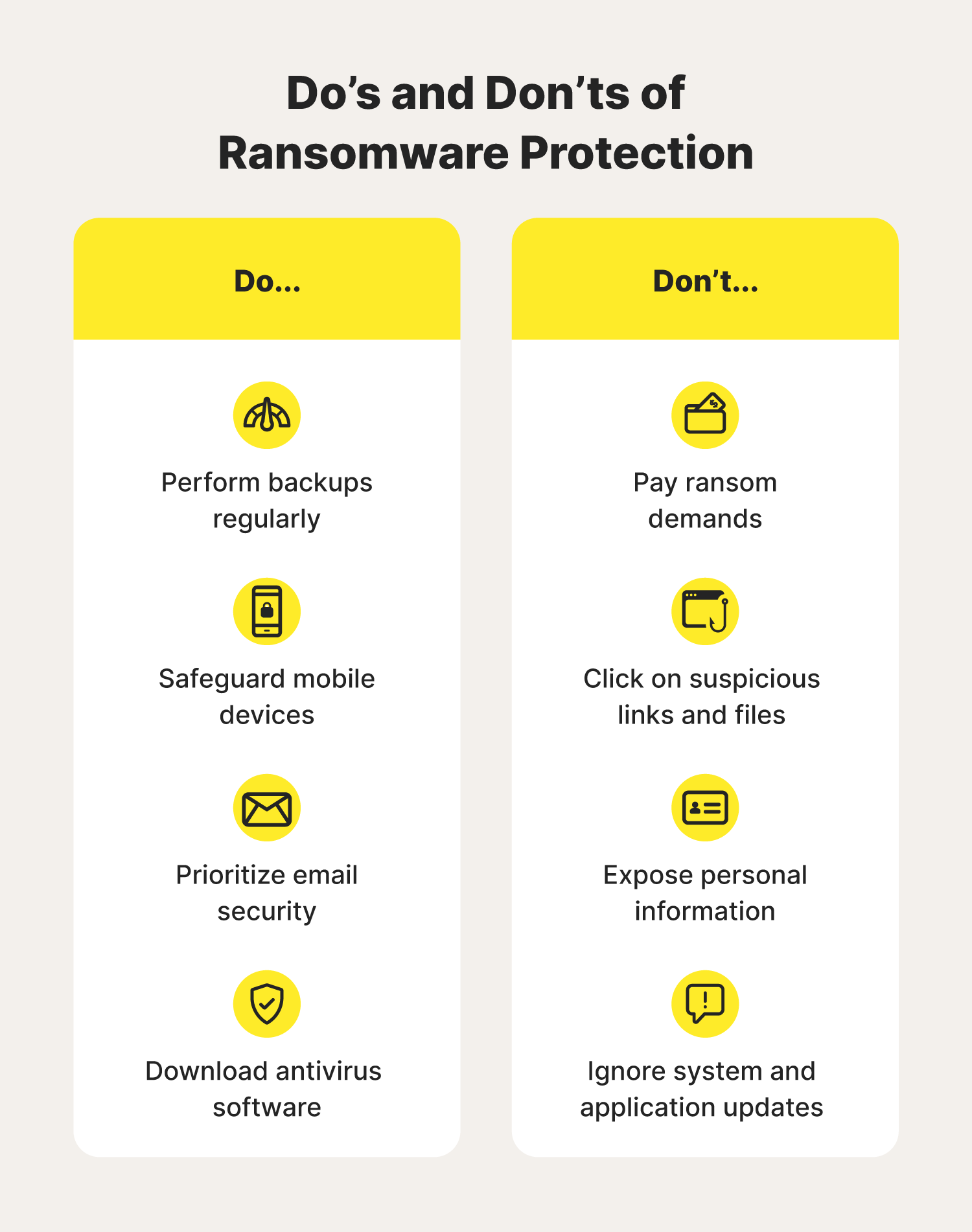
How to avoid ransomware: 9-step guide for 2024 - Norton
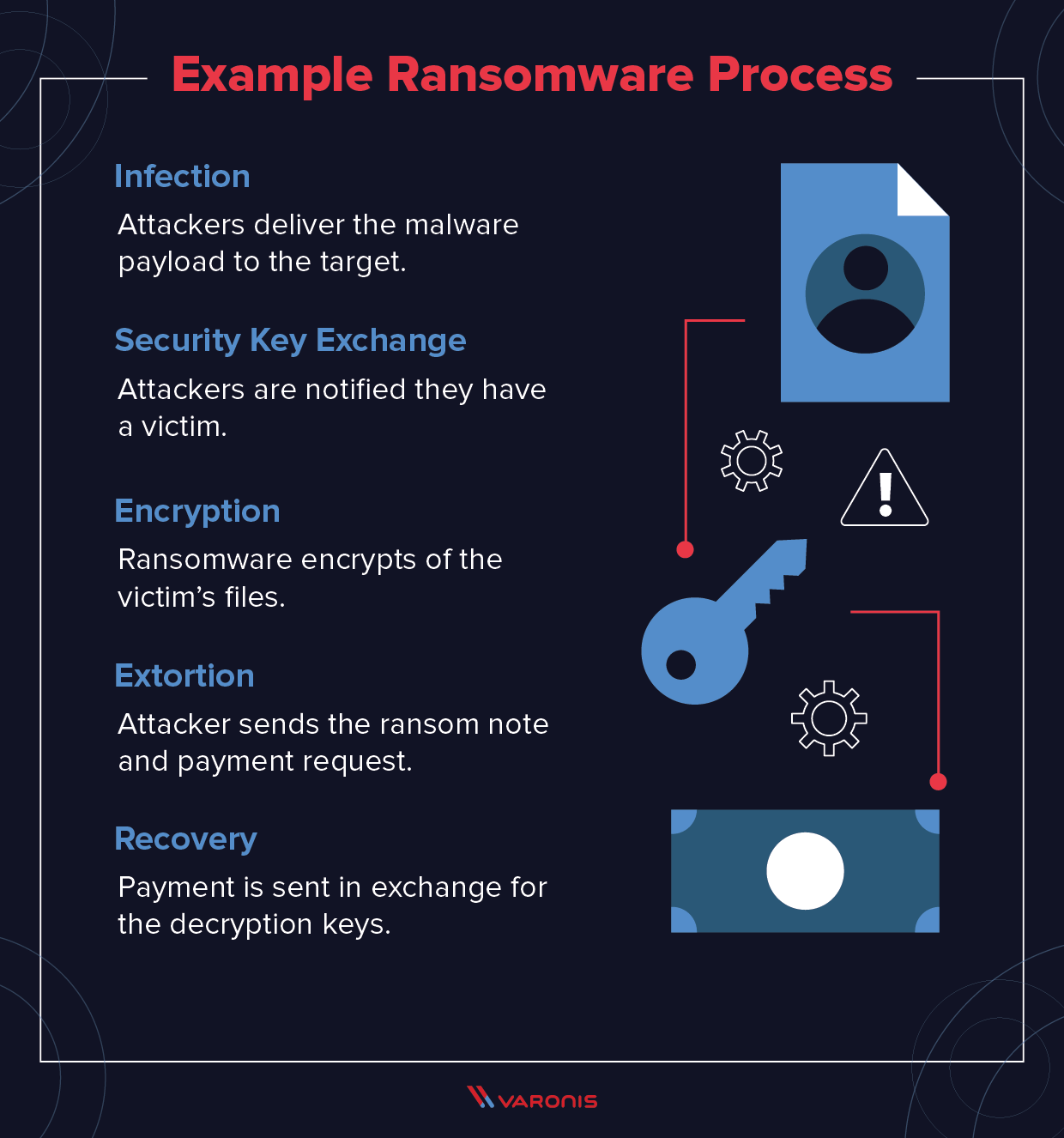
How To Prevent Ransomware: The Basics
Lumu Documentation

What are Indicators of Compromise (IoCs)? A Comprehensive Guide - SentinelOne

Enterprises must fight the vicious trifecta of ransomware to avoid calamity - Here's how to do it - HFS Research

Dark Web Profile: NoEscape Ransomware
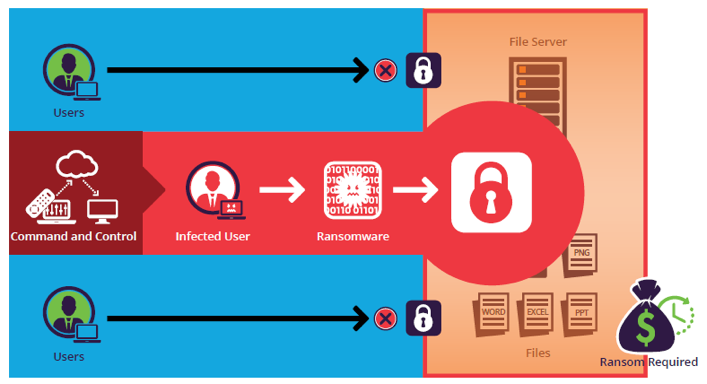
What is Ransomware, Attack Types, Protection & Removal
These 5 Surging Ransomware Attacks Could Doom Your Organization

The Ransomware Attack Lifecycle from the Defender's Perspective

How to Prevent Ransomware Attacks: Top 10 Best Practices in 2023

Automatic disruption of human-operated attacks through containment of compromised user accounts
de
por adulto (o preço varia de acordo com o tamanho do grupo)