IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
Por um escritor misterioso
Descrição
Nozomi Networks Labs analyzes new modification techniques malware authors use to evade detection and analysis tools.
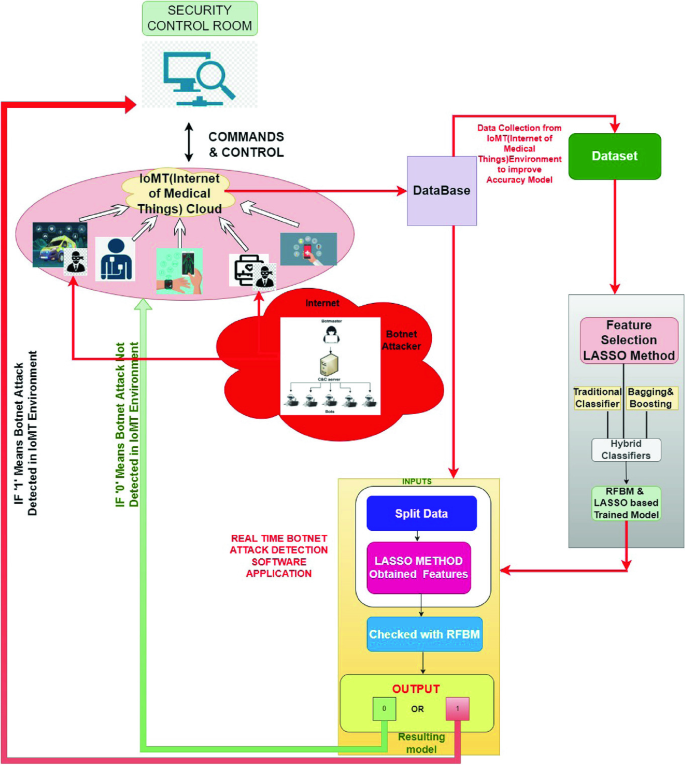
Botnet Attacks Detection Using Embedded Feature Selection Methods for Secure IOMT Environment
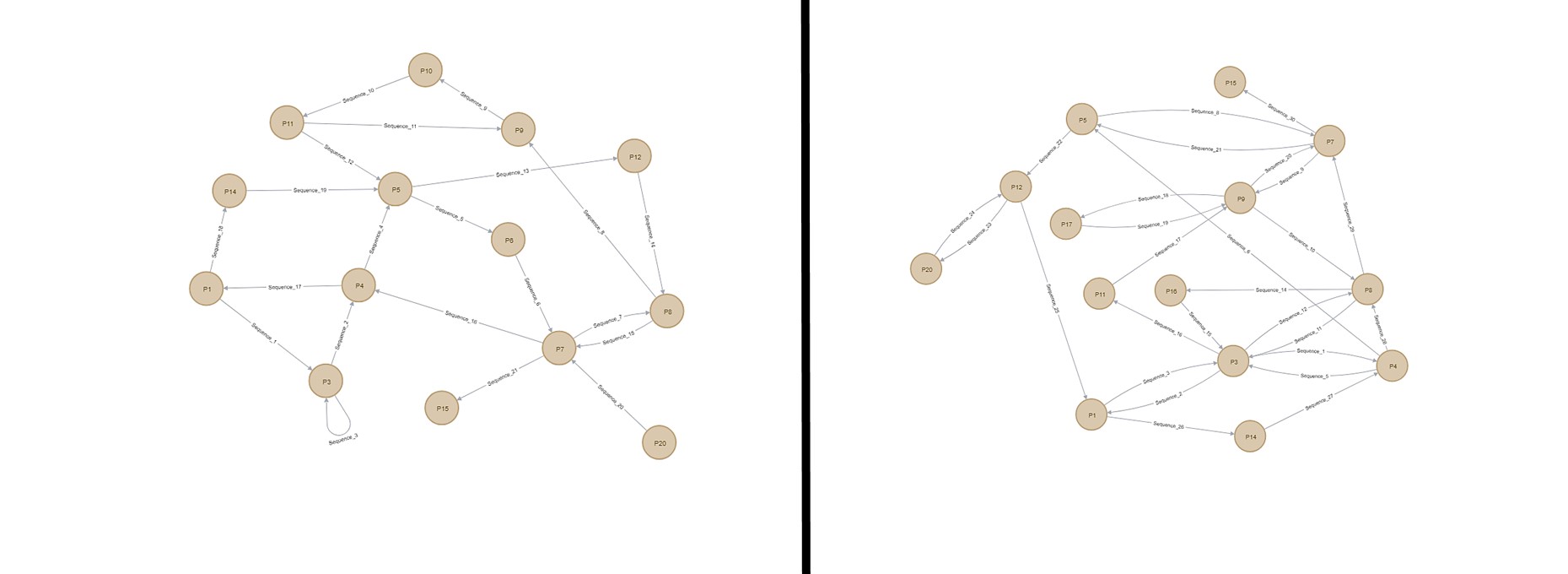
Identifying malicious IoT botnet activity using graph theory

JSAN, Free Full-Text

IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
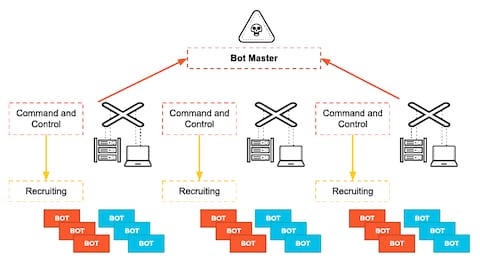
What is a Command and Control Attack? - Palo Alto Networks

IoTEnsemble: Detection of Botnet Attacks on Internet of Things
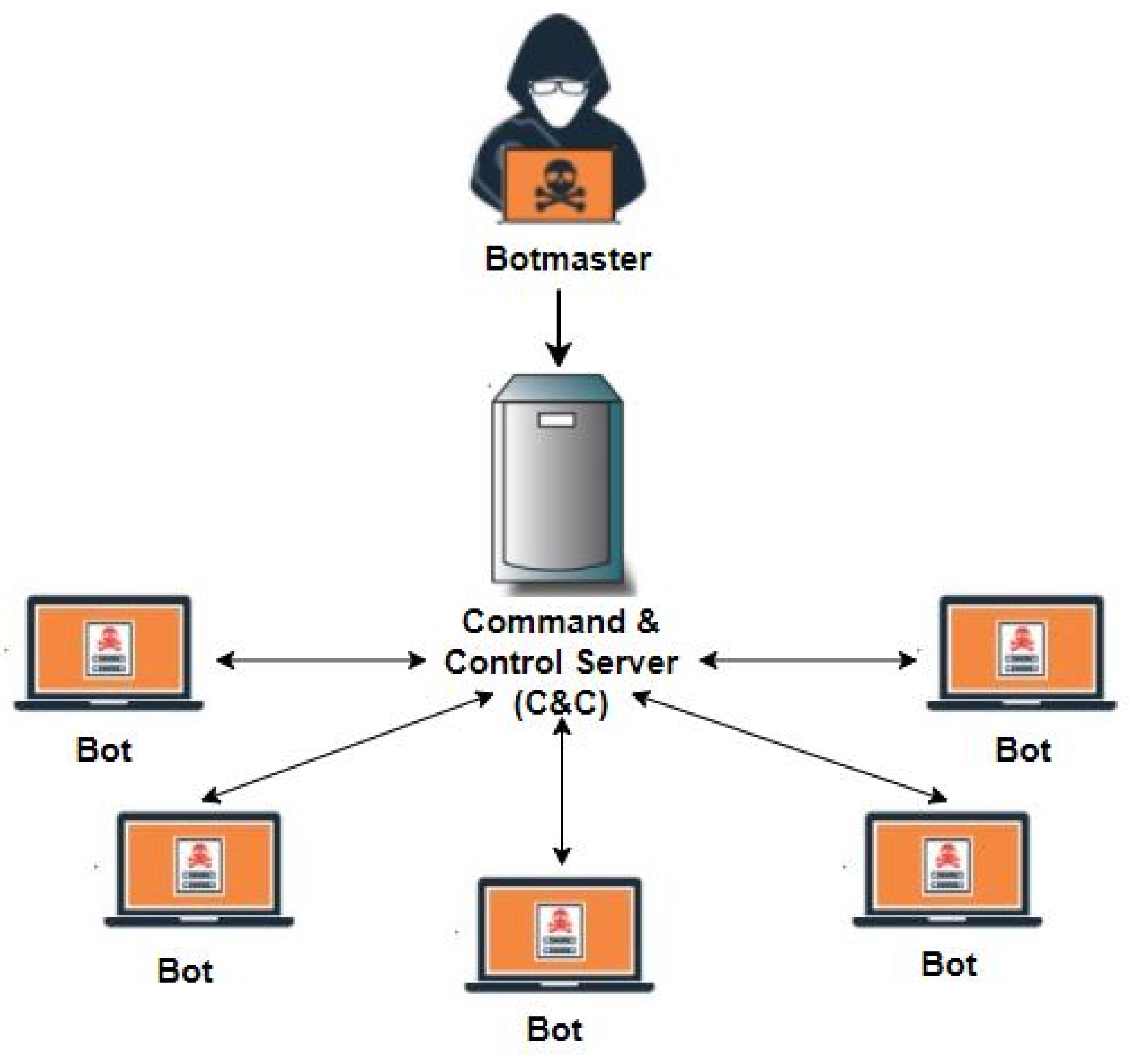
Symmetry, Free Full-Text
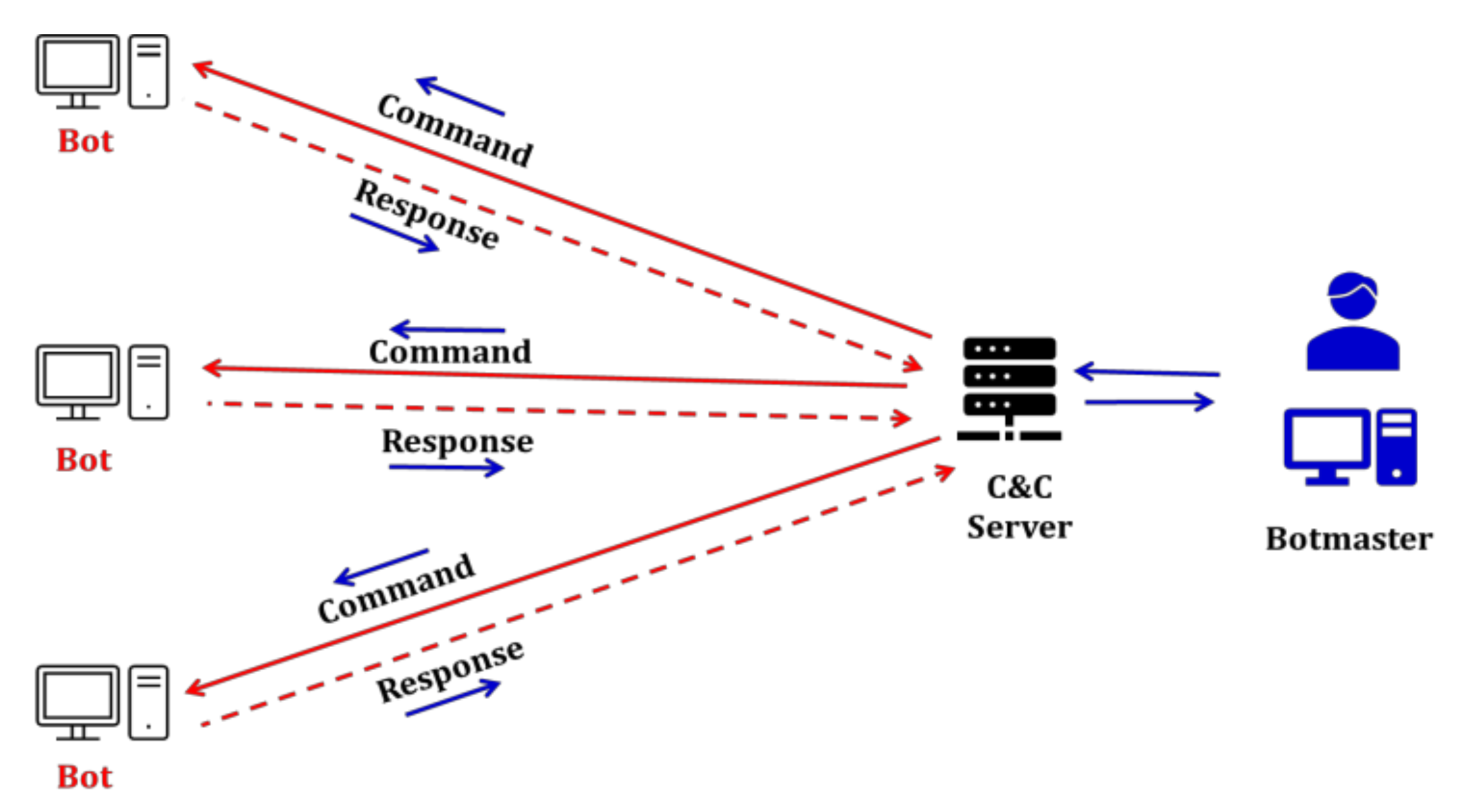
JSAN, Free Full-Text
A DDoS attack scenario in IoT networks as a Botnet to target legitimate

ACM: Digital Library: Communications of the ACM

IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
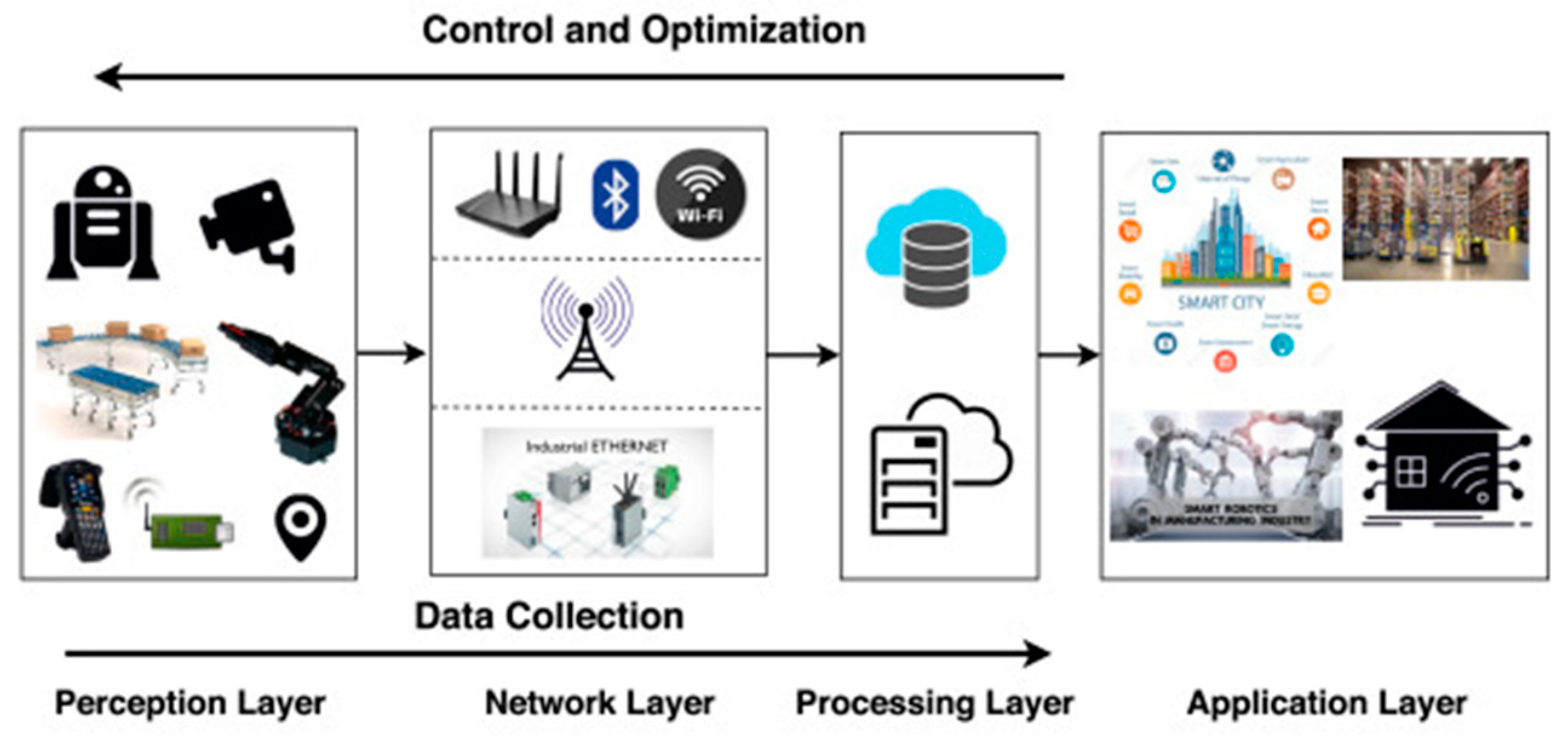
IoT, Free Full-Text

Adversaries' Evasions are Growing Faster than Defenders' Detections - Part 2
de
por adulto (o preço varia de acordo com o tamanho do grupo)