Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Descrição
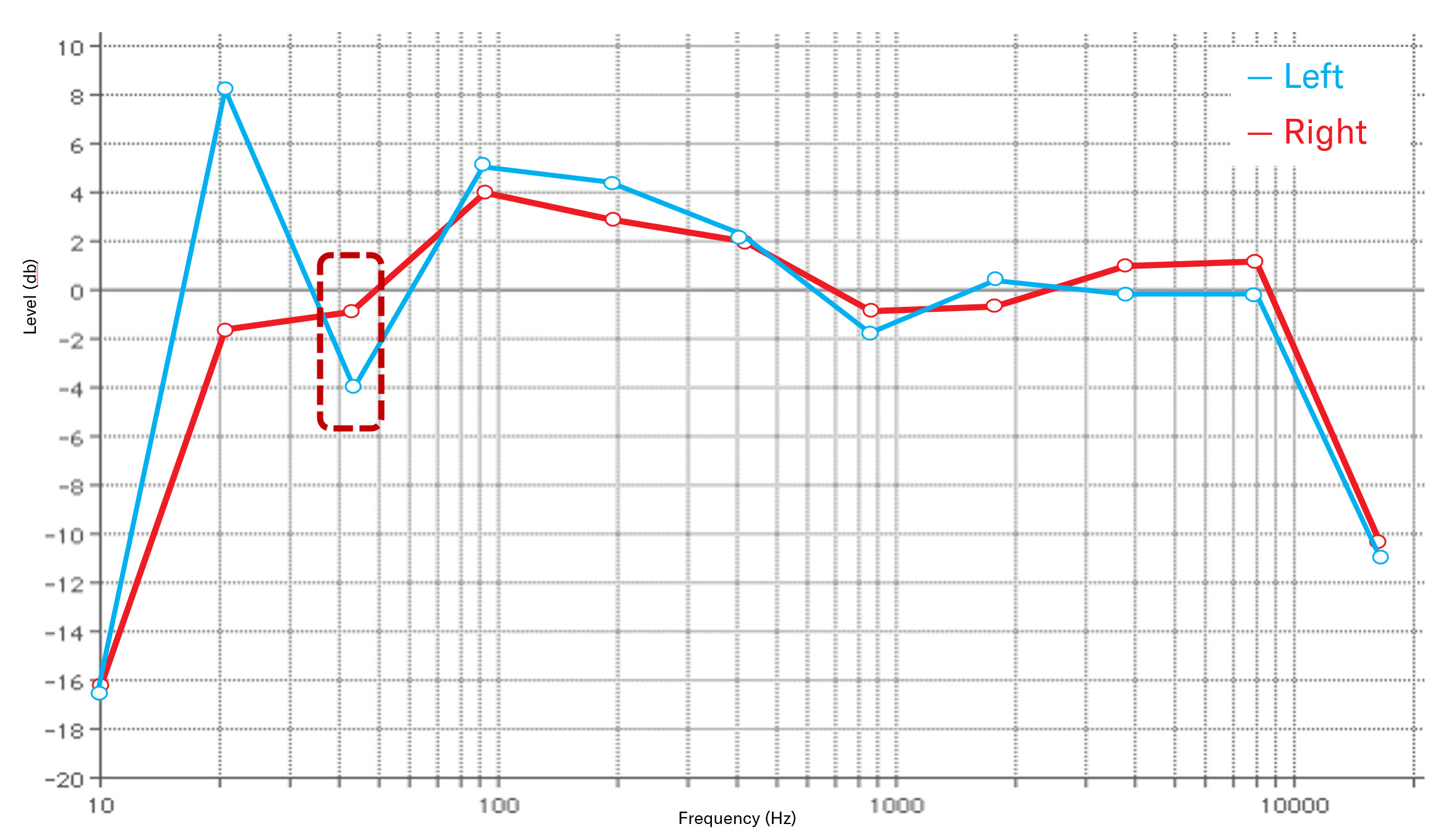
In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.
Using the Firefox Profiler for web performance analysis - TIB AV-Portal
Reverse Engineering: Binary Security, by Totally_Not_A_Haxxer

Kodeco Learn iOS, Android & Flutter
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I
Used Book in Good Condition Highlight, take notes, and search in the book

Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation

Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation: 9781118787311: Computer Science Books @

Blue Fox: Arm Assembly Internals and Reverse Engineering: Markstedter, Maria: 9781119745303: : Books

Reverse Engineering Coin Hunt World's Binary Protocol, NCC Group Research Blog

testar – scriptless testing through graphical user interface - Vos - 2021 - Software Testing, Verification and Reliability - Wiley Online Library

Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend
de
por adulto (o preço varia de acordo com o tamanho do grupo)