Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Descrição
Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..

Application Level Hijacking Using Proxy Hacking - GeeksforGeeks
How Credential Stuffing Bots Bypass Defenses
How to Bypass Cloudflare in 2023: The 8 Best Methods - ZenRows

What Is Credential Stuffing?
The Economy of Credential Stuffing Attacks
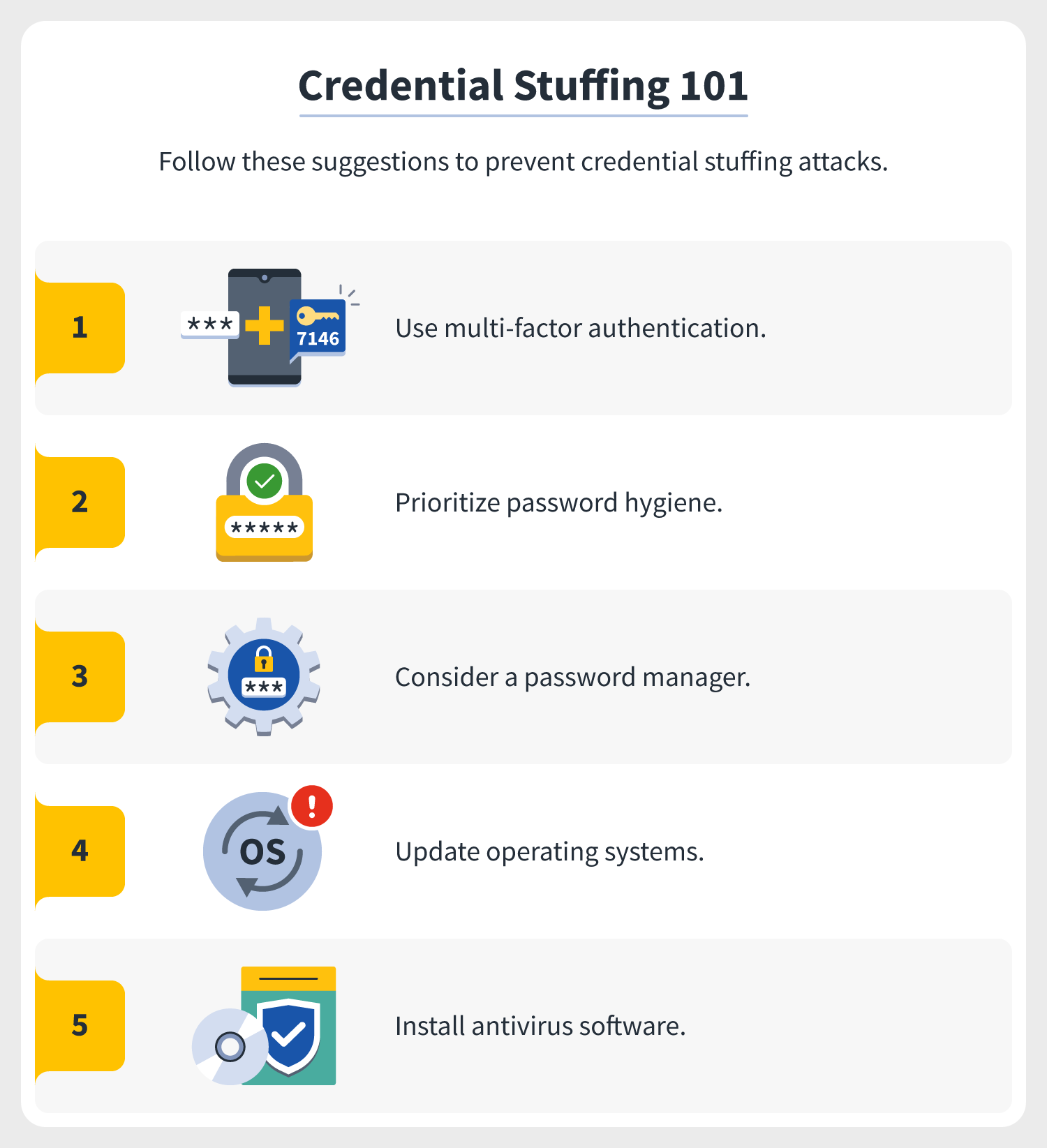
Credential stuffing simplified + attack protection tips

The State of Credential Stuffing and the Future of Account Takeovers.

How to Overcome Credential Stuffing Attacks, by Kuba Zarzycki
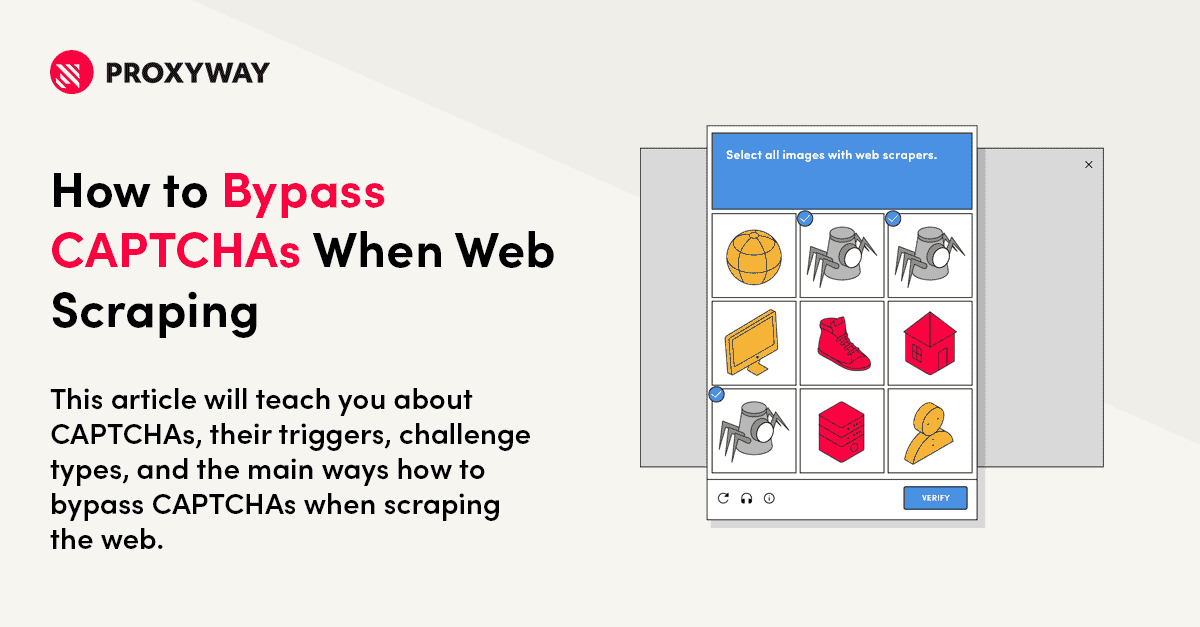
How to Bypass CAPTCHAs When Web Scraping - Proxyway

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools
Protecting Against Credential Stuffing: Lessons from the Paypal Breach
The Ultimate Guide to Avoiding CAPTCHAs in Web Scraping
Captcha Solver: Auto Recognition and Bypass
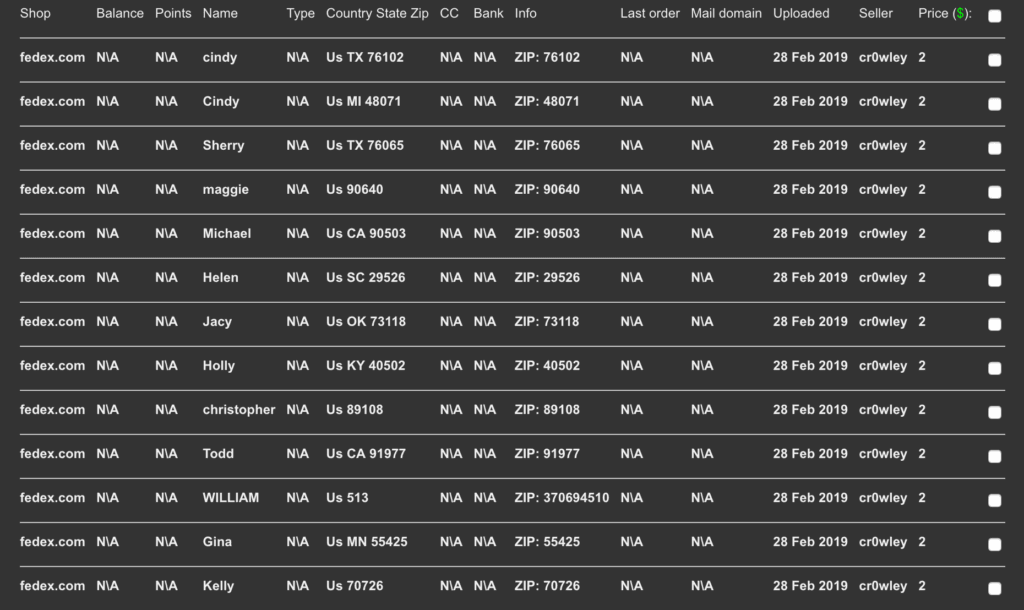
The Economy of Credential Stuffing Attacks

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools
de
por adulto (o preço varia de acordo com o tamanho do grupo)